Detecting sensitive information within the Exchange Online Mail

Hi! Welcome to a new post on the Aleson ITC`s blog. In today’s post we are going to show how to integrate Microsoft Information Protection sensitive data types with Exchange Online email flow rules.
Preventing sensitive information from our organization from being shared in communication channels such as email is a task that we must consider crucial as part of our security strategy. But What can we define as Sensitive Information? Within Microsoft Information Protection we can have a wide variety of templates that define sensitive information, as examples we have:
- Bank accounts
- Credit/debit card numbers
- Passport IDs
- Azure AD Client Secrets
- Storage Account Keys in Azure
For the complete list of the types of sensitive information that Microsoft offers us by default, we can consult the Microsoft Purview administration portal. In addition to these predefined types of information, it is possible to generate new types of information based on the needs of each organization.
Integration within a flow rule
Whether we use Microsoft templates or self-defined information types, here are the steps to integrate them into a mail flow rule:
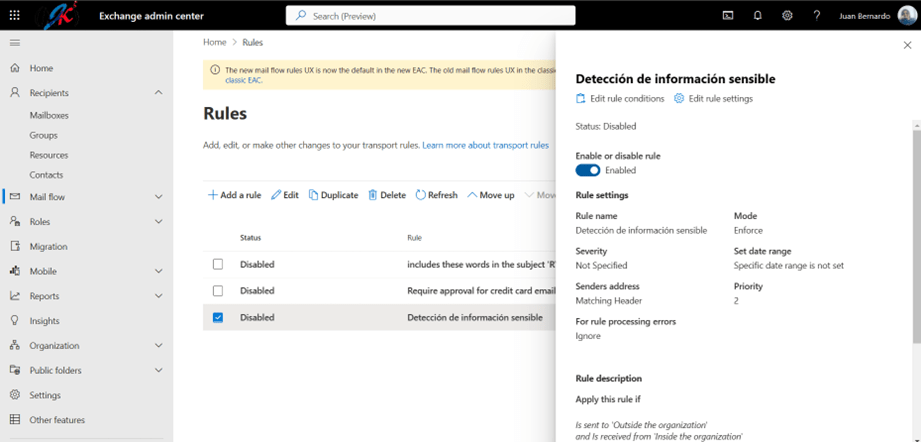
- In the Exchange Online administration portal, we select Mail Flow and then Rules. In this section, we can see a list of the mail flow rules that are currently configured in our environment. At the top, press the Add a rule button.
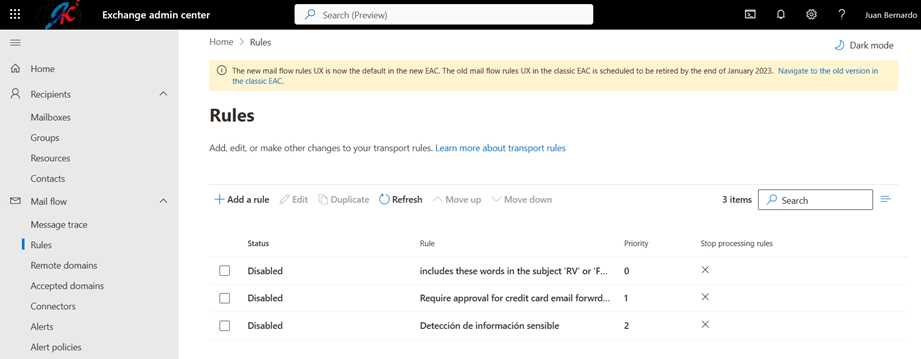
- In this new screen we will see the wizard for creating our rule, it is divided into 3 steps. The first is to define the conditions under which the rule should be executed. As the main condition, we will select the values “The message” and “Contains any of these types of sensitive information”.
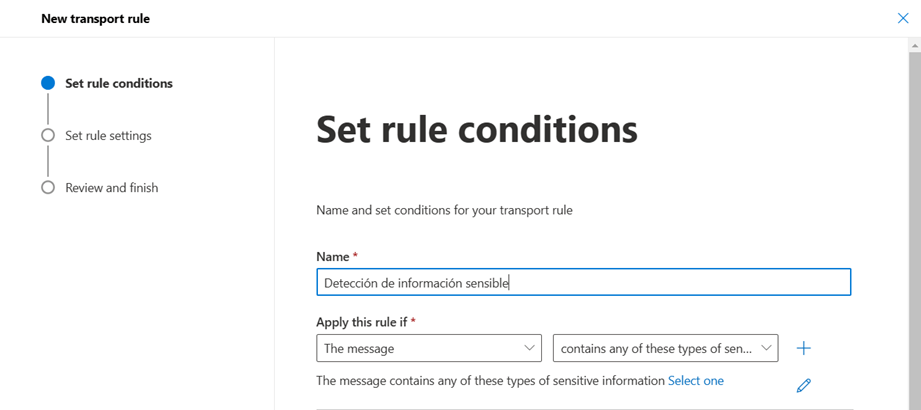
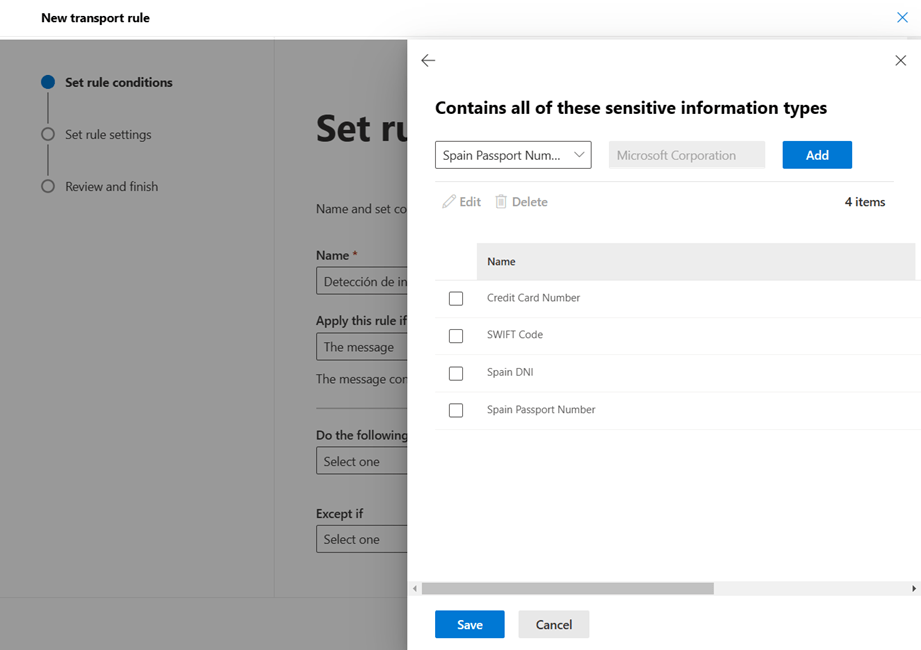
- By selecting these 2 values, a drop-down menu will be displayed in which we can choose the types of information that we want to detect with this rule.
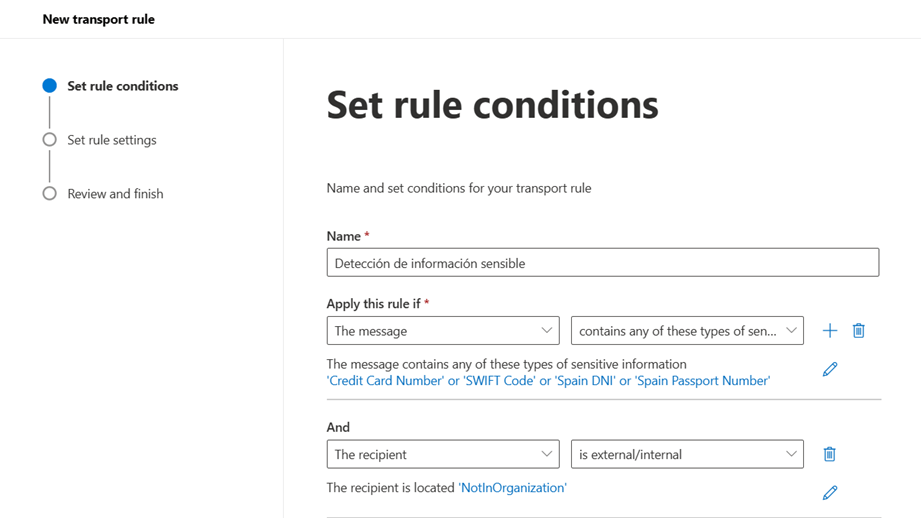
- In addition to this condition, we can add more conditions to our rule so that, for example, it is only executed when the recipient of the email is external to our organization or is a specific person. With the rules editor we can contemplate a wide range of scenarios.
- Once we have established the conditions under which our rule will be executed. The next step is to define the action to be performed. In this case we can also choose one or more actions to perform, among which are:
- Redirect the message to an administrator seeking approval
- Block message
- Apply some warning message
For this example, we will select the option to block the message:
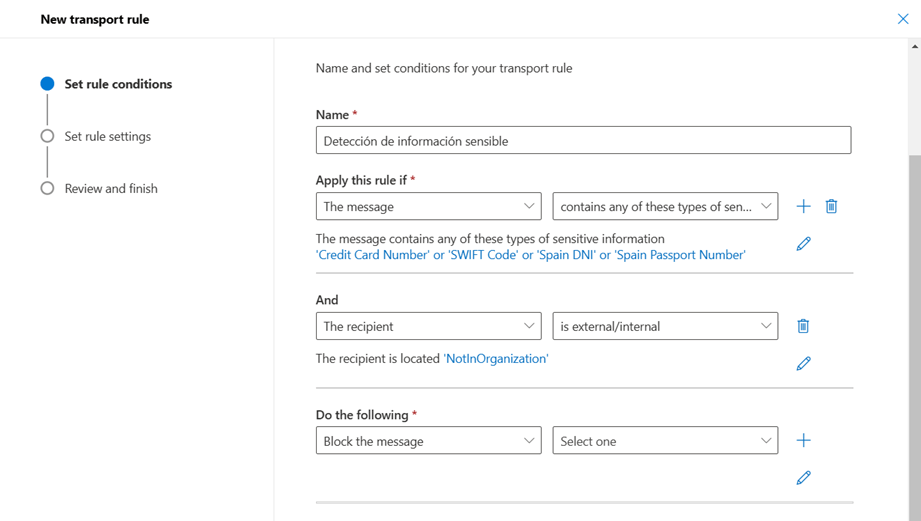
- If necessary, specific exclusions can also be added to the rule based on the message properties.
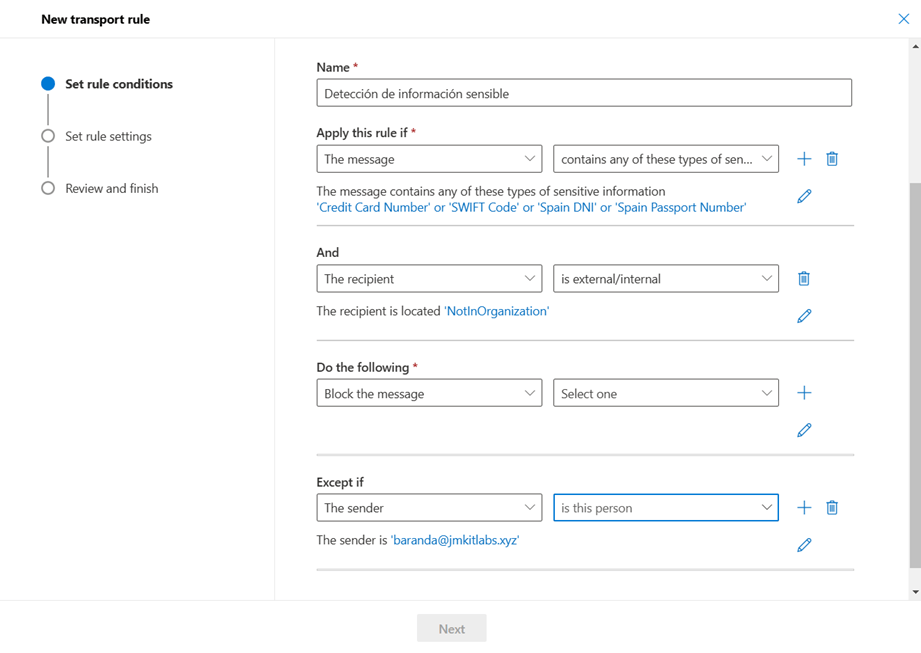
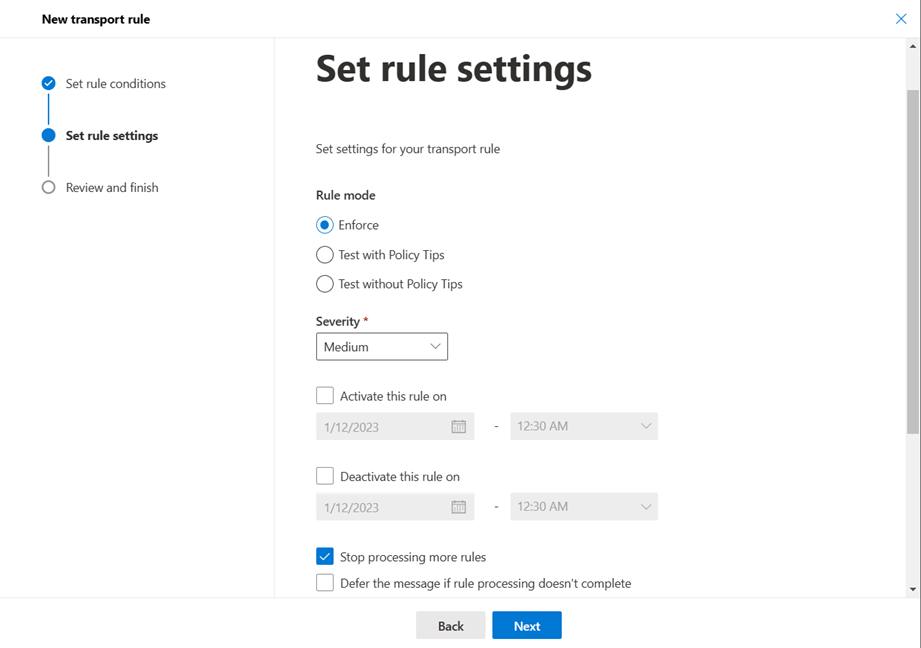
- The second step within the wizard consists of establishing certain settings on the rule such as:
- Rule severity
- Start date
- end date
- Stop the execution of other rules once this one has already been executed
- The last step of the wizard only shows us a summary of how our rule is configured. After validating that all the settings are correct, all that remains is to press the finish button.
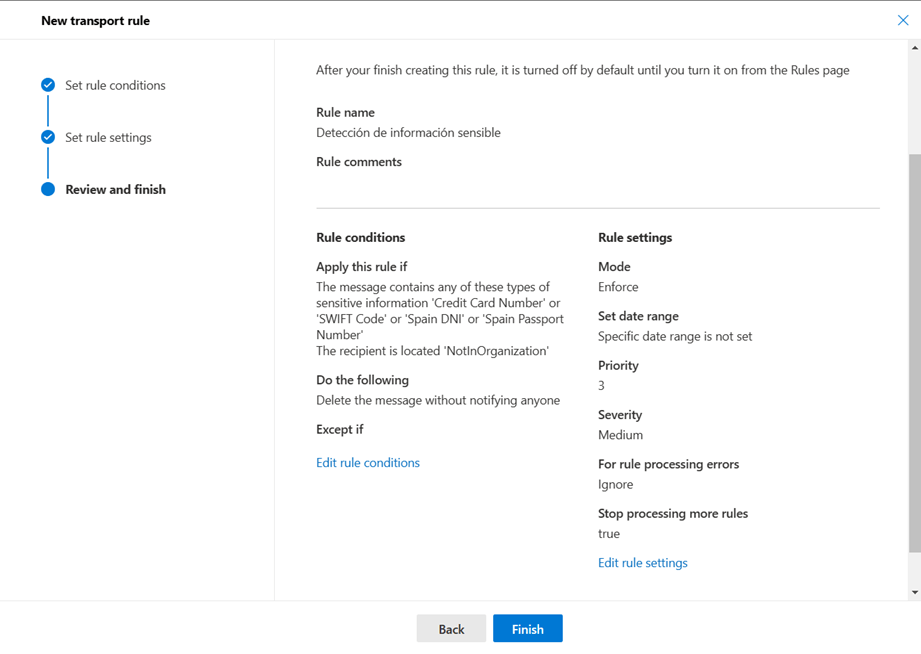
Imporatant!
By default, new mail flow rules are created disabled. Therefore, for these to start running, we must activate them manually from the list of rules.
And here is today’s post, I hope this entry will be of help to you within the security strategy in your organization.
You may be interested in our latest posts:
Knowing the latest news of 2022 for Microsoft Teams
Avoid problems in your SQL Server Migration with Data Migration Assistant (DMA)
Know the Waiting Stadistics or Waits for SQL Server
If you need help with any deployment within the Microsoft 365 security platform, contact us.

Security Engineer.

